2 min read
New in Binalyze AIR v1.8.0: Wazuh integration support and more
![]() Amina Zilic
:
Fri, Sep 10, '21
Amina Zilic
:
Fri, Sep 10, '21

Binalyze AIR v1.8.0 RC is now available.
The full production version of AIR 1.8.0 will be available on 18th August.
You can update directly from your product (shown below) or download it from the website here.
Making a big step towards automated incident response implementation includes the necessity to integrate your organization’s security information event management (SIEM) with proactive digital forensic solutions.
Having Binalyze AIR integrated into your SIEM allows you to react in real-time by starting an acquisition on the endpoint whenever there is a suspicious activity detected by the SIEM. By creating a simple rule, AIR acquires evidence and stores it in the chosen evidence repositories.
Wazuh integration
Wazuh is one of the most popular open-source SIEM worldwide. For that reason, we decided to incorporate Wazuh integration out-of-box into this product release to make daily DFIR duties more manageable and efficient. As you might already know, AIR can be integrated with any Webhook source but having an out-of-box integration makes things a lot easier.
How to integrate Wazuh with AIR?
Integration of AIR with Wazuh is possible via the “Integrations” section of the AIR console.
Steps to Integrate
Step 1: Create a Trigger for Wazuh
-
Visit the Webhooks page in Binalyze AIR,
-
Click the “+ New Webhook” button on the upper right corner,
-
Provide a self-explanatory name (examples: RDP Brute Force Trigger, Phishing Detected Trigger, etc.),
-
Select “Wazuh: Wazuh AIR Integration” as the parser for this webhook,
-
Select an Acquisition Profile to run when Wazuh activates this webhook,
-
Select the Ignore option or leave with its default value (defaults to 24 hours for recurrent alerts for a single endpoint),
-
Provide other settings such as Evidence Repository, CPU Resource Limit, Compression & Encryption to use or let AIR configure them automatically based on the matching policy
-
Click the “Save” button,
-
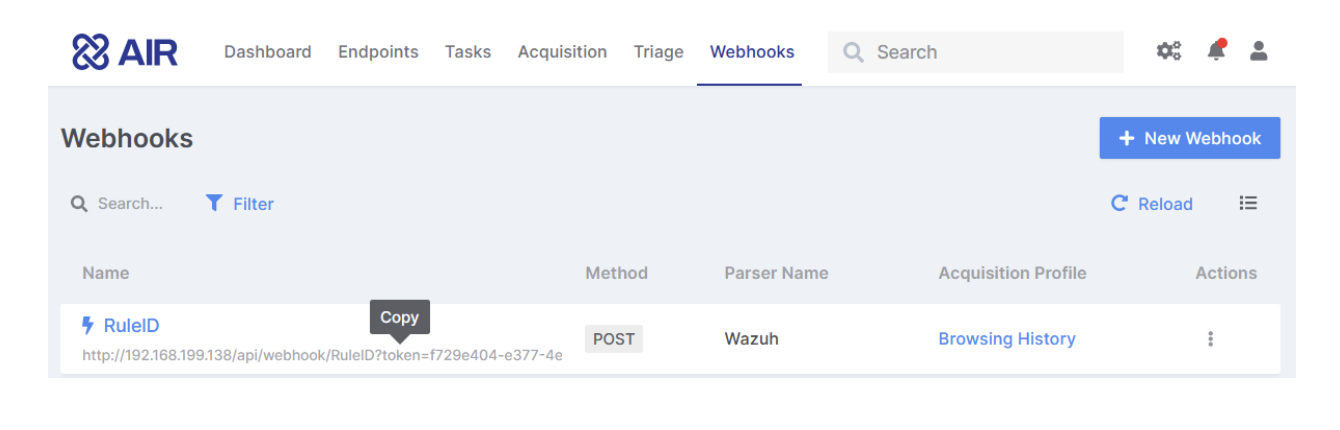
Hover your mouse over the link below the Webhook name and double-click to copy (see below)
Step 2: Add the Integration Settings in Wazuh
- Open the ossec.conf file with a preferred text editor and add the following line to the end of the file before saving and closing the ossec_config. The name must begin with ‘custom’ i.e. custom-air1, custom-air2 etc.. For our example below we have used the name ‘custom-air’, for detailed information, please see the Wazuh Documentation.
.png?width=600&name=CleanShot-2021-08-10-at-10.40.35@2x%20(1).png)
Step 3: Creating the scripts in Wazuh
Every time the relevant rule_id is triggered, a bash script named custom-air is executed. Create a file named custom-air in /var/ossec/integrations/ paste the following script. For detailed information, please refer to the Wazuh Documentation.
-
Create a python script named custom-air.py /var/ossec/integrations/ and paste the following script. The script runs another python script and makes a request to the air server.
-
The scripts must be placed in /var/ossec/integrations, have the same name as indicated in the configuration block, contain execution permissions, and belong to the root user of the ossec group.
A step-by-step guide on how to integrate Wazuh with AIR can be found on this link.
Automated incident response
One of the main drivers behind our development at Binalyze is automation to drive efficiency. Naturally, SIEM integrations are part of this concept to improve the security posture of your organization by automating tasks within Binalyze AIR to react as fast as possible whenever an incident occurs and deliver enhanced forensic capabilities.
We already support a number of SIEM integrations out-of-the-box, with many more on the way, as well as a simple, bespoke webhook integration that can be deployed in minutes.
Binalyze AIR comes with out-of-the-box support for the following widely used SIEMs:
If you want to add a new integration, that we don’t have out-of-box support for, you can do that in the AIR Webhooks section in just a few steps.
-
Open your AIR dashboard, go to the Webhooks section and click on “+ Integration”
-
When creating a new integration give it a name and choose the generic parser option as shown in the image below
-
Next, copy the generated URL and paste it into your SIEM solution.
Integrating automated digital forensic solutions into your SIEM system can vastly improve your security information handling and cybersecurity posture.
Try Binalyze AIR today, download it.









