Some History
It was around 7 years ago when I analyzed my first CryptoLocker which was just a prototype full of mistakes and weird stuff. My first reaction to this ‘new’ way of making money was “Well, not an art piece compared to what we have been dealing for the last three years (mostly low-level kernel-mode rootkits) but it is still promising”.
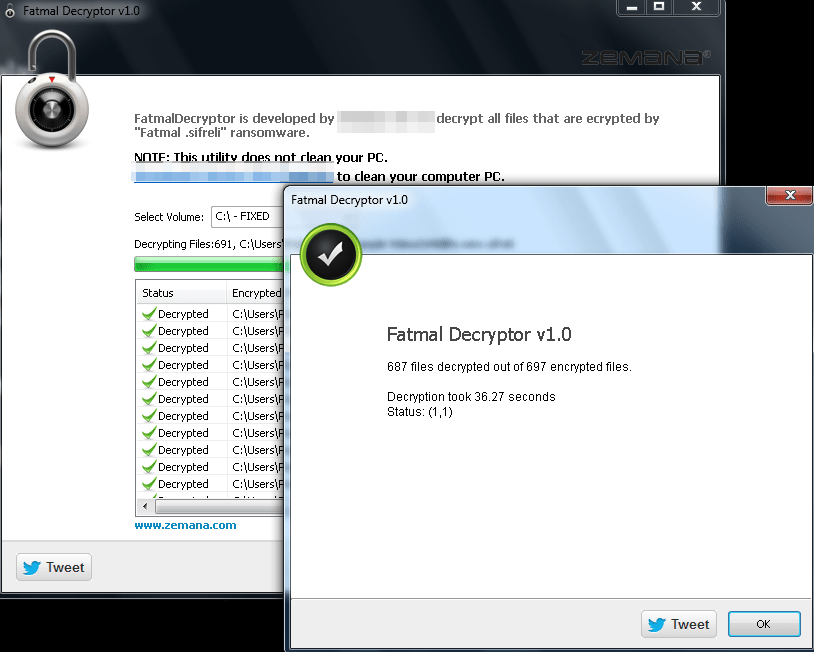
Back in the day, a quick look into the code was more than enough to create a decrypter. But how? The problem was that the attacker was using AES 256 in CTR mode and he was only encrypting the first 2MBs of the files for making the encryption process faster. Finding that all the affected systems had a video file named “Wild Life” which was also encrypted by the CryptoLocker, we have created a decryptor for FREE (zero bitcoins). This was –as far as I know– the first freely available decrypter for a crypto-locker case. The funny thing is, the author of crypto locker fixed his cheap code by switching to AES CBC mode after finding out that the victims were using our tool to decrypt encrypted files, not his :):):)
7 years fast forward: Our partner CyberArtsPro calls our support team on a Sunday morning in an urgency stating that IREC TACTICAL can not collect evidence from a crypto-locker infected machine?! We were surprised at first but a quick investigation made it obvious that the crypto locker was not only encrypting the user files but also the evidence collected by IREC.
The moment I was informed about the situation, my reaction was “All right. Let the war started.” which led to the development of our new feature “SHIELD”.
What is SHIELD?
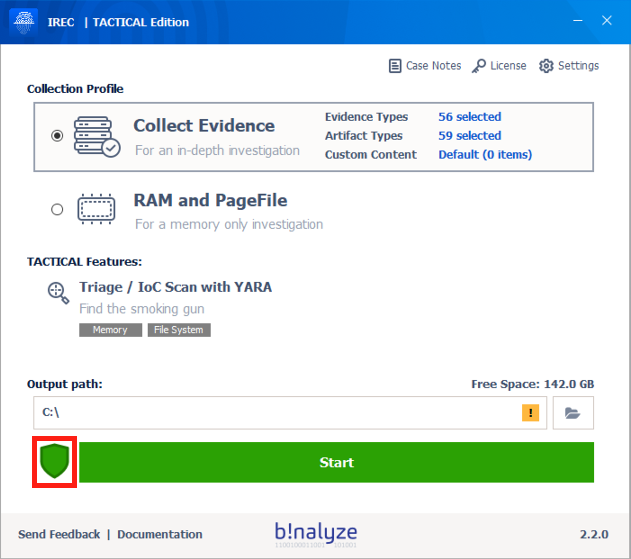
SHIELD is a kernel-mode component added to IREC version 2.2.0 protecting all the evidence collected by our solution regardless of the media it resides in. At its core, it is a Mini Filter driver attaching to all volumes on the affected machine for blocking access of any other application except IREC thus enabling our users to securely collect evidence.
At this point, you may be asking what is the point of collecting evidence from an already infected machine. Aren’t crypto locker authors using asymmetric encryption for their ransomware? They mostly do but not always. Remember that most cybercriminals are in chase of easy money which makes them susceptible to making a lot of mistakes. As an example, in a recent case, our partner DIFOSE was able to retrieve the decryption key of VEAM Backups just by using IREC’s Clipboard content collection feature. (Note to attackers: DO NOT copy & paste encryption keys please type them patiently if you want your Bitcoins.)
How to use?
Starting with version 2.2.0, SHIELD will be enabled by default and will stay active until you disable it by clicking the shield icon on the main page of IREC or by clicking one of the two buttons on the acquisition summary page (Open Output Folder / Open Case Html). Please note that IREC will only protect the case files it collects regardless of the location they reside (USB Drive or a network share) which is the reason we suggest you use a USB drive or a network share dedicated for this purpose only.
You can download IREC 2.2 Preview version from the link below: https://cdn.binalyze.com/irec/IREC-2.2.0(Preview).exe
Enjoy SHIELD and stay safe at home!
Dear Attacker;
Please accept our apologies for decrypting your so-called ultra-secure encrypted files.









