Original Post
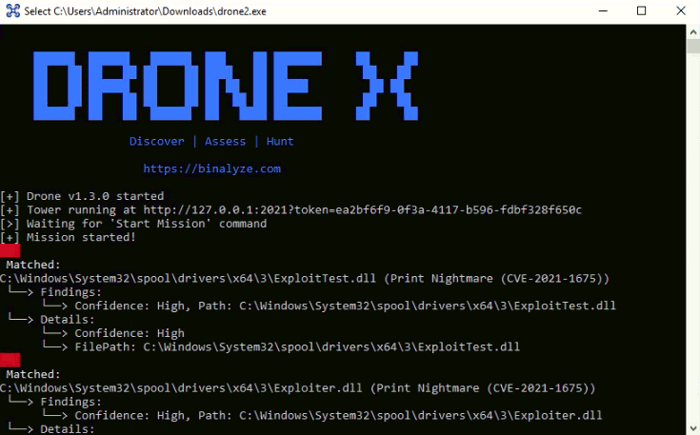
Proof-of-concept exploit code has been published online today for a vulnerability in the Windows Print Spooler service that can allow a total compromise of Windows systems. The vulnerability impacts Print Spooler (spoolsv.exe), a Windows service that serves as a generic universal interface between the Windows OS, applications, and local or networked printers, allowing app developers to easily initiate print jobs.
The service has been included in Windows since the 90s and is one of the operating system’s most buggy processes, with many vulnerabilities being discovered across the years, including bugs such as PrintDemon, FaxHell, Evil Printer, CVE-2020-1337, and even some of the zero-days used in the Stuxnet attacks. CVE-2021-1675, the latest in this long line of Print Spooler bugs, and was initially discovered by security researchers from Tencent Security, AFINE, and NSFOCUS earlier this year.