Reduce Incident
Response Time
Accelerate and streamline cyber investigation
workflows with automation
Trusted by Organizations Worldwide
Incident response automation benefits
Reduce time and costs to close investigations
Augment SOC efficiencies and capability
Boost proactive assessment capabilities
Combat data overload and analyst burnout
Anatomy of Breach Investigations
A traditional incident response workflow can take 16 hours at minimum to execute - and often a lot more. What if there was another way to accelerate the start and overcome one of the biggest challenges facing teams today - starting an investigation with the right visibility.

Addressing unique
investigation challenges
Once detected, a new set of considerations and challenges emerge
when you move to the investigation phase.
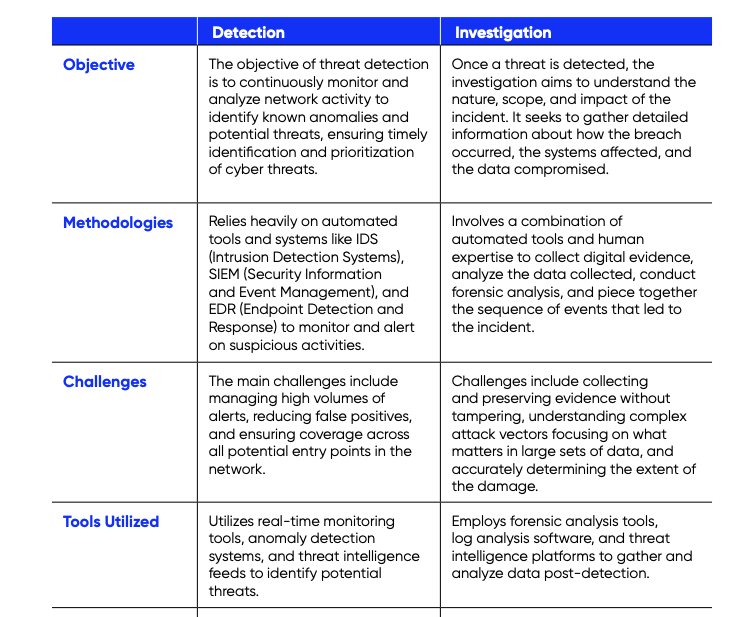
| Detection | Investigation | |
|---|---|---|
Objective |
Continuously monitor and respond to security incidents to prevent or mitigate attacks, involving a cycle of improvement and the application of telemetry, analytics, and alerting to identify potential threats. |
Once a threat is detected, the investigation aims to understand the nature, scope, and impact of the incident. It seeks to gather detailed information about how the breach occurred, the systems affected, and the data compromised. |
Methodologies |
Relies heavily on automated tools and systems like IDS (Intrusion Detection Systems), SIEM (Security Information and Event Management), and EDR (Endpoint Detection and Response) to monitor and alert on suspicious activities. |
Involves a combination of automated tools and human expertise to analyze the data collected, conduct forensic analysis, and piece together the sequence of events that led to the incident. |
Challenges |
Continuously monitor and respond to security incidents to prevent or mitigate attacks, involving a cycle of improvement and the application of telemetry, analytics, and alerting to identify potential threats. |
Once a threat is detected, the investigation aims to understand the nature, scope, and impact of the incident. It seeks to gather detailed information about how the breach occurred, the systems affected, and the data compromised. |
Tools-Utilized |
Utilizes real-time monitoring tools, anomaly detection systems, and threat intelligence feeds to identify potential threats. |
Employs forensic analysis tools, log analysis software, and threat intelligence platforms to gather and analyze data post-detection. |
ON-DEMAND WEBINAR
Reduce Investigation and Response Times with Streamlined Analysis
Watch now an engaging webinar featuring Craig Guymon, Solutions Architect Director, and Sophie Bovy, Sr. Product Marketing Manager, as they provide an in-depth overview and live demo of Binalyze AIR's Investigation Hub. Discover strategies to elevate your investigative processes, significantly reduce investigation times, and improve visibility across all data points.
Platform coverage
.png?width=734&height=103&name=LOGOS%20platform_Grey%20(1).png)
Ready to supercharge your investigations?
Start your free trial and experience the power of automated investigations.
No credit card required. Quick setup. Instant impact.
Cut weeks off your IR workflow — Try AIR for free.
Binalyze AIR Guide
Download our DFIR Guide and learn more how you can elevate your incident response processes.









