
Some history;
Digital forensics is 40 years old, so are the methods…”
Do you remember how much time you spent acquiring an image, taking it to your lab, processing it with powerful machines running traditional forensics solutions in order to get a timeline of events that took place? Editing CSV files, exporting Event Logs, dealing with time zones, trying to combine them into one large file, using open source tools, spending hours, and hours, and hours if not days, losing the most precious resource of all: “Time”. Now, it is time to change it!
Let me begin with how it started. We released IREC TACTICAL almost 3 years ago to address the problems of our industry. The concept was simple: Changing IR evidence acquisition into a 1-click job. So we would speed up, decrease the need for communication and make the “collection” phase of IR easier than ever.
Although easy to describe, it was not a simple task. Did we manage it? With the great support of our users, we absolutely did! There is now a solution for 1-click evidence collection. With IREC TACTICAL, you can collect more than 260 different pieces of evidence with the click of a mouse. Besides collecting almost everything you would need to understand what went wrong on that endpoint, it also creates a self-contained HTML report, time-stamps it for non-repudiation and protects the collected evidence against ransomware modifications!
Era of Automated IR
TACTICAL was great and it still has a heavy development roadmap that adds great features with every new release. However, in cases we were involved, there was one another huge problem: Remote evidence collection and the lack of automation. When you have one endpoint, you can collect evidence one way or another. Make some phone calls, send some emails, ask IT admins and finally RDP into the machine and run IREC. But if there is more than one endpoint located in different places, continents and time zones, the responders still had a lot to do alongside scratching their head. So we developed Binalyze AIR, the most comprehensive automated IR and remote forensics solution on the market that can integrate with any RESTful trigger source.
Once integrated (that takes only 5 minutes), 03:00 AM in the morning, your SIEM creates an alert and, voila, AIR starts doing its job automatically! Just like having a 24/7 available first responder waiting for your call, going to the crime scene, capturing photos of every single corner in just minutes. When your analysts arrive in the morning they have all the evidence of what happened on that endpoints. But what happens if more than one endpoint involved in the case? Just like having 2 crime scene photos captured from different places in different time zones. You spend hours combining these two together. What if you have 3, 4, 5 of these… You already know the answer. This was the question we were asked by a significant number of our customers that led to the development of TimelineIR.
Meet TimelineIR
I am sure you can name a bunch of solutions that can create a timeline starting from traditional forensics solutions to open source command line tools. They are all great but if the clock is ticking, you need something much faster and easier! Something that won’t fight against you, something that will speed you up and show you what you need without making you deal with nitty-gritty details…
TimelineIR is the brand new feature of Binalyze AIR that:
-
Creates a timeline investigation “remotely” in just 5 minutes,
-
Collects almost everything from an endpoint that has a timestamp attribute. To name a few, Processes, DLLs, Shellbags, Shimcache entries, Prefetch files, Browser History for all major browser, Relevant Event Logs, Autorun Entries, Services, Downloaded Files, Recycle Bin, SRUM and so on…
-
Presents this is in a web-based interface, that is ultra-optimized for speed and ease of use,
-
Lets you flag events making them immediately visible to the other analysts working on the same investigation,
-
Enables filtering for specific events based on event type, date and time, computer name, user name and event data,
-
Lets analysts add milestones based on what they hear from the affected users or customers,
-
Decreases the time of investigation by multitudes,
-
Thus, fixing the biggest problems of Enterprise IR Investigations.
Action!
Having all these said, now it is time to showcase how easy it is.
-
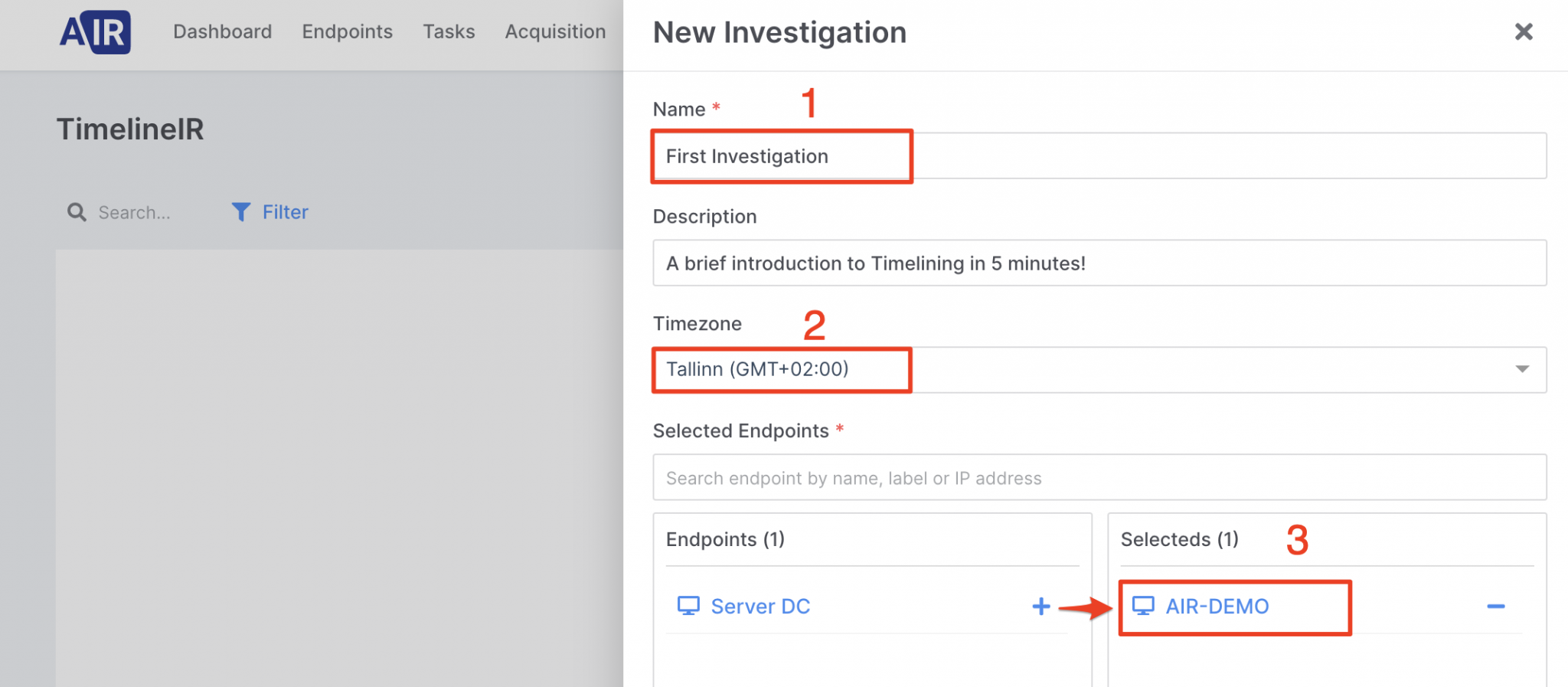
Create an investigation named “First Investigation”,
-
Select the timezone of the investigation,
-
Add an endpoint to investigation,
-
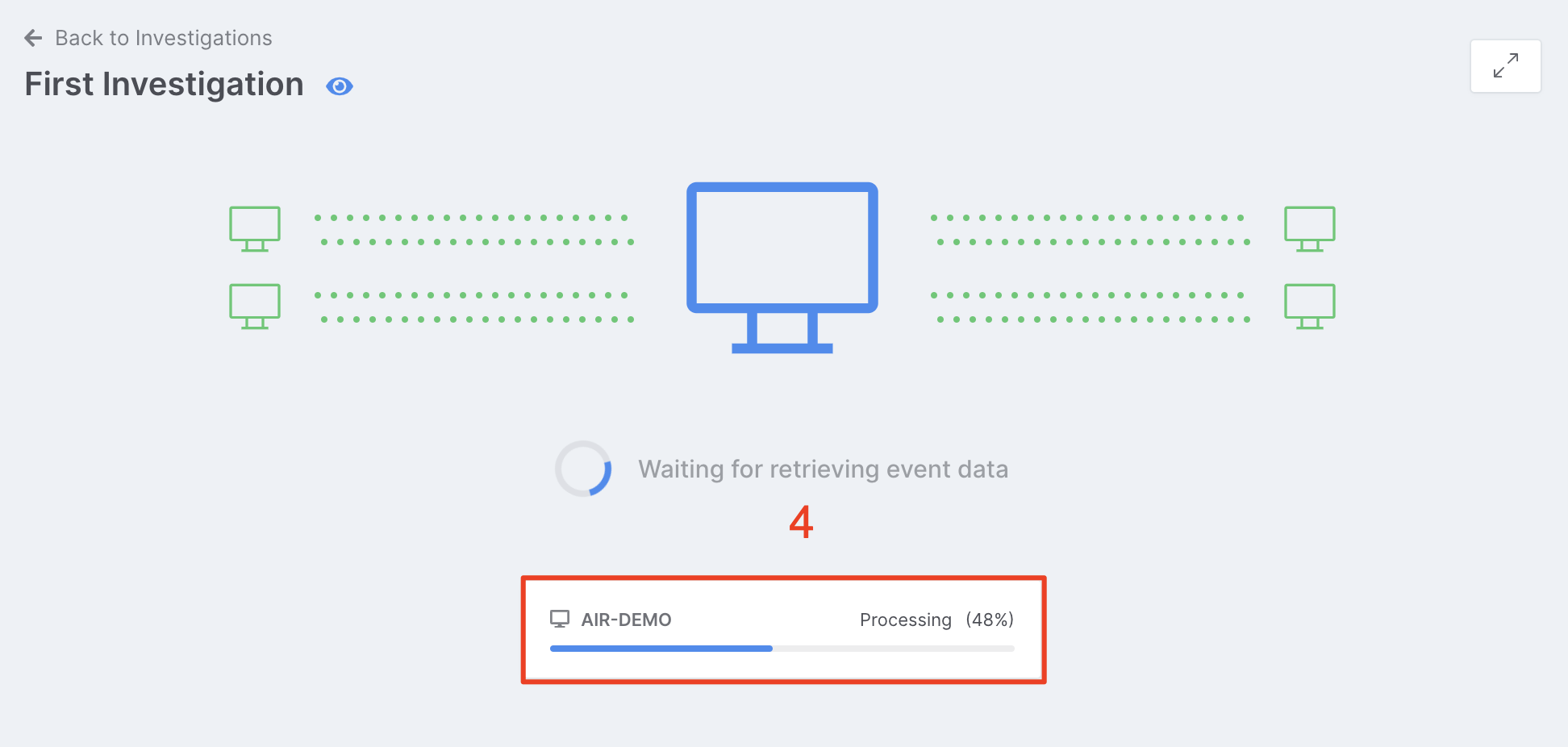
Wait for the processing of forensic evidence to complete in “5 minutes”,
-
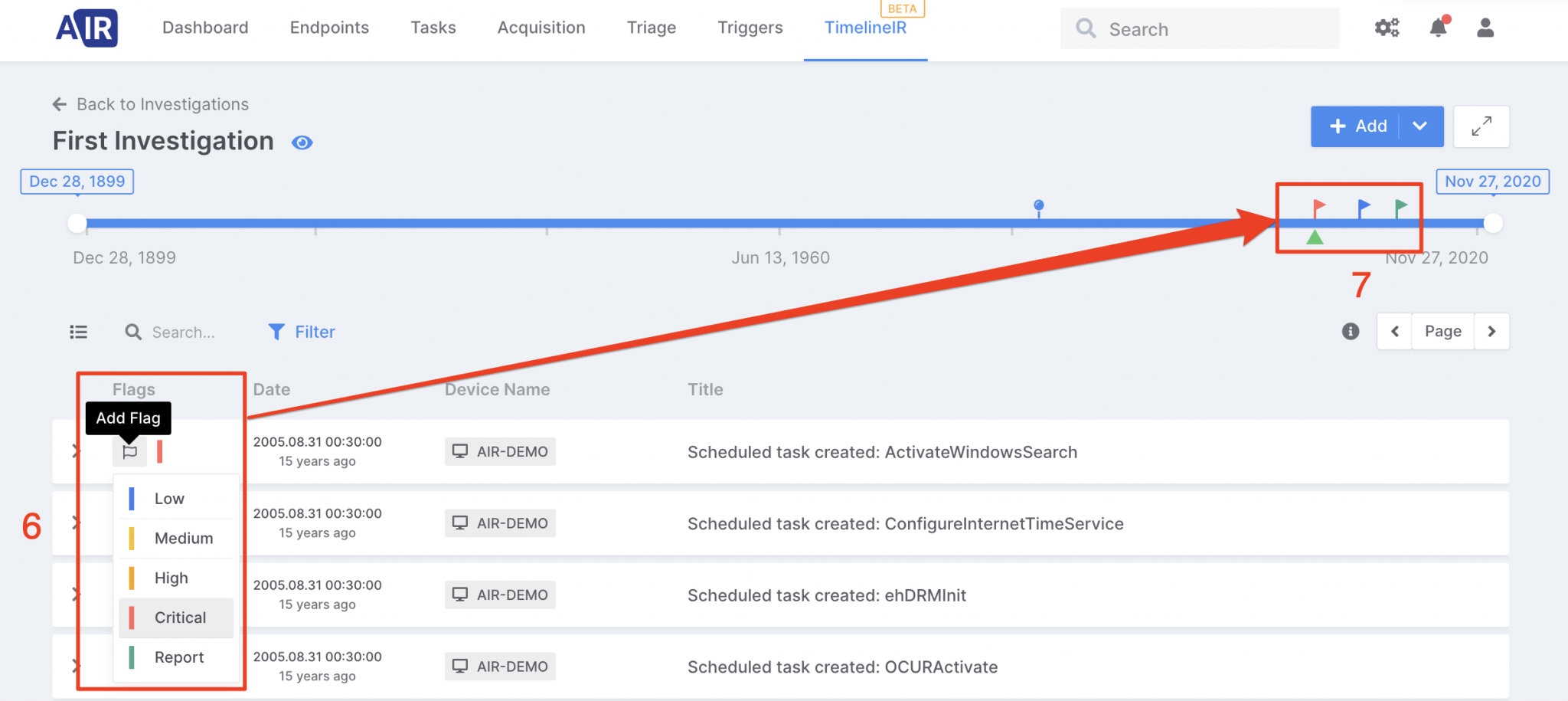
Easily navigate by dragging the green arrow in the navigation band or click it for selecting the target date,
-
Flags some events, mark some of them to be reported,
-
Click a flag for time traveling,
-
Add milestones that would provide useful for a better understanding of the case,
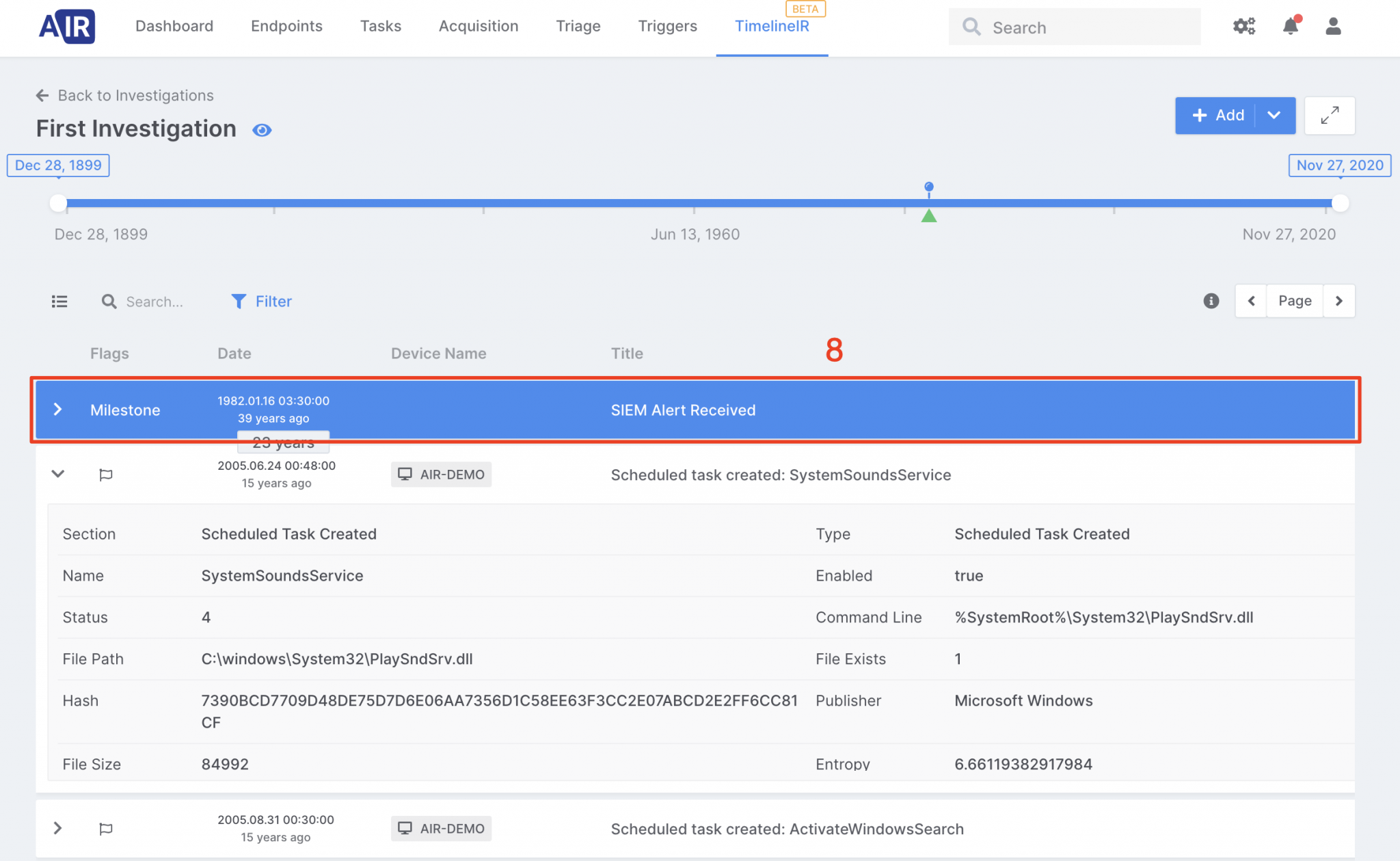
- When required, enrich your investigation by adding new endpoints.

Try it now!
Feeling excited? Download AIR now and easily create a timeline investigation using the link below:










