
We’re excited to announce the release of AIR v4.23! This version introduces powerful new features, including enhanced Windows Event Log support and other improvements such as, AIR’s File Explorer now supporting disk image mounting from Azure Blob storage.
In this release, by fine-tuning and enhancing AIR’s Sigma engine, we’ve made significant backend improvements that reduce unwanted noise and false positives by around 40%. This reduction is crucial because it allows analysts to spend less time sifting through irrelevant data and more time identifying and addressing real threats. As we continue our work, future updates will push this reduction even further, to 70-80%, helping analysts focus on critical events even faster. Our goal is to streamline the investigative process, enabling quicker and more accurate responses to incidents.
These features and improvements are designed to enhance your investigative workflow, save time, and provide even more digital forensics precision.
Let’s dive into the key enhancements in this release starting with the standout feature for the handling of Windows event logs:
Improved Windows Event Log Collection
This is the outstanding new feature in AIR v4.23 which enables users to fully customize event log collections based on specific channels, event IDs, and collection parameters, making investigations more efficient and precise.
When discussing Windows Event Logs, it’s important to understand two key concepts: channels and event IDs.
-
Channel: A channel in Windows Event Logs refers to a specific "log" or source of events. Windows organizes event logs into several channels, each dedicated to logging specific types of events. Examples of commonly investigated channels include:
-
Application: Logs events from applications running on the system.
-
Security: Logs security-related events, such as logon attempts or resource access.
-
System: Logs system-level events, including hardware failures and system services.
-
Setup: Logs setup-related events, typically related to Windows installation and updates.
-
-
In the context of Binalyze AIR, channels can be essential when filtering or triaging specific logs during forensic analysis. Using channels, investigators can isolate relevant events to gain more efficient insights.
-
Event ID: An event ID is a unique identifier for a specific type of event within a channel. Windows assigns an event ID to categorize the nature of the event. For example:
-
Event ID 4624 in the Security channel represents a successful user login.
-
Event ID 6006 in the System channel indicates a system shutdown.
-
-
Event IDs are critical for identifying and understanding specific actions or issues in the system. In forensic investigations with solutions like Binalyze AIR, event IDs are used to pinpoint exact events relevant to a security incident, helping investigators build timelines and correlate suspicious activity.
In Binalyze AIR's Investigation Hub, filtering by channels and event IDs allows analysts to narrow down logs quickly to focus on those most relevant to an investigation.
Key Features introduced in AIR v4.23:
-
AIR will now allow users to collect and present all event logs OR
-
Define specific channels for event log collection.
-
Users can select event IDs from the AIR list of over 200 of the most commonly used in DFIR or manually add custom channels and event IDs.
-
With event ID selections made an additional parameter is required:
-
Select the number of records to collect OR
-
Select date ranges for log collection, allowing for targeted log retrieval.
-
How It Works:
A new Event Log Records configuration tab has been added to the “New Acquisition Profile” wizard:

If you are already building an acquisition profile you will eventually come to the EventLogs section and you will not notice a new configuration button which will take you to the Event Log Records tab as discussed above:

To enable this feature switch on the EVT Log Records by toggling on the switch shown below and then either:
-
Choose from a predefined list of 201 event IDs or,
-
Input custom channel and event IDs using the Add New Event Type option.
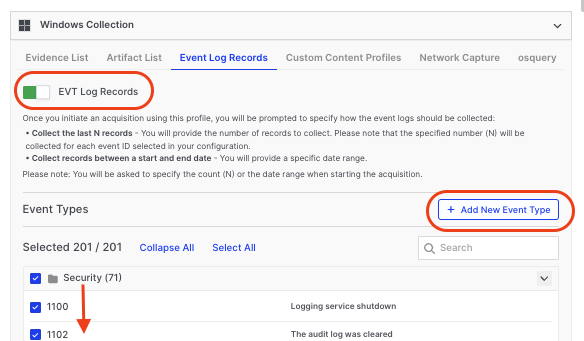
The example below demonstrates how to manually add an event ID that is not included in the 201 provided by AIR. This is typically only necessary for rare, specialized cases, as the 201 event IDs cover the most common scenarios comprehensively:

Once configured, the new Acquisition Profile will be saved and can be reused in future investigations by selecting it from the Acquisition Profiles Library.
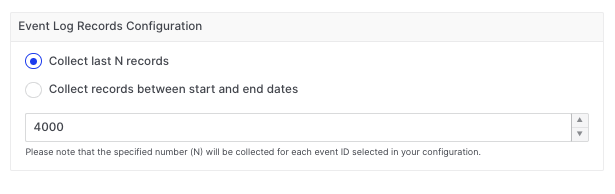
When running an Acquisition Profile that includes event log records, users must select between two additional Event Log Records Configurations options:
-
Collect last ‘N’ records – This gathers the most recent ‘N’ records for each event ID, in the example below this is set to 4000:
-
Collect records between start and end dates – In the example below we have used the date/time picker to choose the last 24 hours option and you can see those dates/times are automatically populated in the start and end boxes:
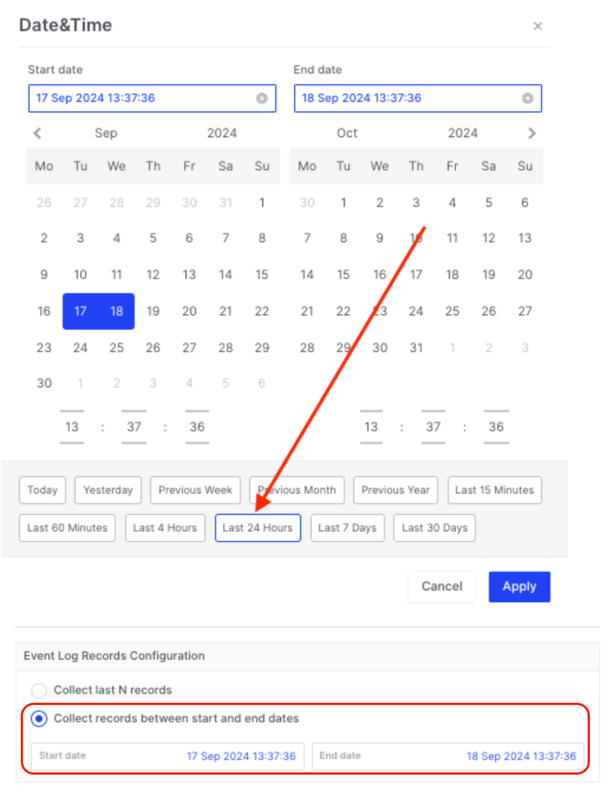
The dates and times selected in the 'picker' align with the target asset's system date and time settings, as displayed in the browser.
These features enable highly focused and relevant data collection, drastically reducing the manual effort needed to filter out unnecessary data and ensuring that critical events are captured during investigations.
Here’s a list of what some may consider the top ten event IDs often used to support DFIR Investigations:
-
Event ID 4624 - Successful Account Logon
Tracks successful user logins, essential for identifying legitimate access. -
Event ID 4625 - Failed Account Logon
Logs failed login attempts, useful for detecting brute-force attacks. -
Event ID 4776 - Credential Validation
Indicates whether a user's credentials were successfully validated by a domain controller. -
Event ID 4688 - Process Creation
Records every process started on the system, useful for spotting suspicious activity. -
Event ID 4648 - Logon Using Explicit Credentials
Detects when credentials are used for network logon, helping track lateral movement. -
Event ID 4663 - Object Access
Logs when an object (like a file or folder) is accessed, crucial for monitoring sensitive data access. -
Event ID 4698 - Scheduled Task Creation
Captures when a scheduled task is created, often used by attackers for persistence. -
Event ID 4719 - Audit Policy Change
Tracks changes to audit policies, which may indicate an attempt to cover tracks. -
Event ID 1102 - Audit Log Cleared
Logs when the security log is cleared, a common indicator of malicious activity. -
Event ID 4672 - Special Privilege Assigned
Monitors when special privileges (like admin rights) are assigned, helping detect privilege escalation.
Scan Local Drives Only for Triage Tasks
With the Scan Local Drives Only feature, users can improve triage efficiency by focusing threat hunting and triage scans solely on local drives, excluding remote external or network drives that often introduce unnecessary data into the investigation. Attached mounted USB drives should be included as ‘local drives’.
Key Details:
-
Available for all AIR-supported operating systems.
-
Disabled by default but can be enabled via the organizational policies page: Settings>Policies>Scan Local Drives Only.

-
It can also be configured when creating individual triage tasks using the custom options:
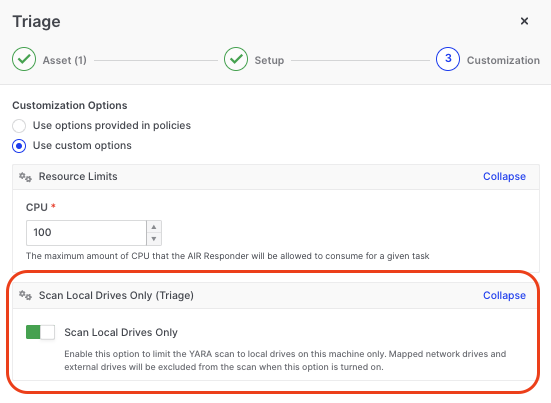
This feature ensures that only relevant data from local drives is collected, reducing noise and improving the speed and accuracy of investigations.
Keyword-List Upload for DRONE Searches
AIR v4.23 introduces the ability to upload keyword list files for DRONE searches, allowing investigators to conduct more focused and efficient searches within their data collections.

Key Features:
-
No character limit for keyword lists, but a 1 MB file size limit applies.
-
Each keyword must be on a new line for proper search functionality.
-
Keyword searches are limited to data within the Case.db (excluding CSV files).
-
This search functionality extends to event log data collected by Sigma analyzers, including:
-
Windows: Event Record Analyzer
-
Linux: Syslog Analyzer
-
macOS: Audit Event Analyzer
-
This feature offers investigators greater flexibility and precision in their searches, significantly enhancing the DRONE module's capabilities. Regex support will be added soon in an upcoming release.
Real-Time Disk Usage Visibility in the Investigation Hub
Managing storage during an investigation is now more intuitive with the introduction of real-time disk usage visibility on the AIR database server. Investigators can easily track storage usage at both the Case and Task Assignment levels, ensuring that resources are optimally managed.
Key Features:
On the AIR Cases page, a new column displays the total space occupied by collections across all assets in a case:

In the Task Details window, users can view the space occupied by the individual Task Assignments:

This visibility helps investigators manage storage more efficiently, preventing potential performance issues caused by overloaded storage environments.
Azure Blob Support for Image Files in AIR’s File Explorer
Many customers store forensic image files and evidence collections in Azure Blob storage.
With v4.23, the AIR File Explorer now supports the mounting/presentation of disk image files stored from Azure Blob storage directly in the AIR console, streamlining access to these files for investigations.

VHD and VHDX Disk Image Support in AIR File Explorer
In addition to the existing support for RAW, E01, Ex01, and VMDK files, AIR File Explorer now supports **VHD and VHDX disk images**. Investigators can create assets from these disk images and browse through their contents, further enhancing the flexibility and usability of the File Explorer:

Summary
With these enhancements in AIR v4.23, we aim to streamline your investigative processes, reduce manual effort, and provide more powerful tools for digital forensics. We’re confident that these new features will make your investigations faster, more precise, and easier to manage.
For more detailed information on these updates or to explore further resources, please refer to our Knowledge Base or if necessary, reach out to our support team.









