
Welcome to the latest evolution of the AIR platform—AIR 4.13—an update that promises enhancements and a transformation in how investigations are conducted. At the heart of this transformation is the redesigned AIR "Investigation Hub," which serves as the command center to elevate all of your investigative activities. This centralized interface seamlessly manages all case-related elements including assets, evidence, artifacts, and triage results, thus streamlining the investigative process like never before.
The Investigation Hub is meticulously organized to provide efficient filtering options and a robust global search feature. This eliminates the cumbersome need to switch between multiple tools or manually integrate information from disparate sources. With additional data sources and enhanced data-importing capabilities, investigators can now augment their analysis with relevant data and context, ensuring access to a comprehensive and continually updated set of information. This dynamic, responsive environment absorbs and consolidates every piece of information and will automatically generate reports as the investigation unfolds, making it a living ecosystem that adapts to the evolving nature of each case.
The launch of AIR 4.13 introduces a fresh user experience (UX) and user interface (UI) in the Investigation Hub, bringing with it new features that prioritize forensic visibility, drive operational efficiency, and enhance collaborative efforts. These updates include a new dashboard, innovative widgets, and enhanced functionalities that make workflows more intuitive and responsive to the specific needs of each investigation.
Significant enhancements in this release also include the ability to integrate user-generated Findings and custom Flags, along with advanced options to exclude non-relevant findings—features that significantly increase the granularity and flexibility of reporting. This allows for quicker, more precise analytical processes, enabling investigators to focus on what truly matters in a sea of data.
Furthermore, AIR 4.13 extends the capability of the platform with the inclusion of new evidence types, integration of osquery into acquisition profiles, and improved isolation controls that ensure essential services remain uninterrupted during critical investigative processes.
As we delve deeper into the functionalities and enhancements of AIR 4.13, we invite you to explore how these changes can significantly benefit your operations. We are eager to hear your feedback and look forward to seeing how these innovative features transform your investigative outcomes.
Features
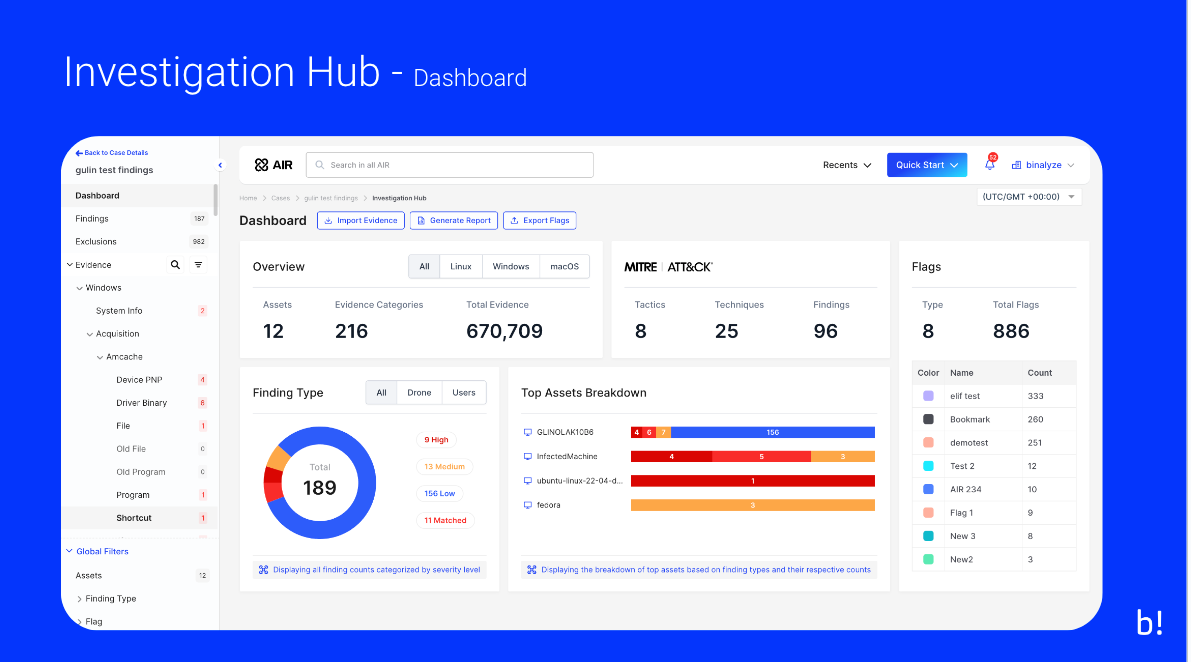
New Dashboard & Widgets
-
Global search with tabbed search for AIR or the Investigation Hub
-
Export user-generated flags to .csv
-
Clickable Finding Types for new re-mapped 4 severity levels:
-
High
-
Medium
-
Low
-
Matched
-
- New user-generated Flags widget
New Secondary Menu

-
The new secondary menu allows:
-
Search for evidence in the comprehensive categories listings
-
Hide empty pages, and categories with no return
-
Show only evidence with Findings
-
Show only the evidence with flags
-
Global Filters for:
-
Assets including the ability to filter by individual taskings
-
Finding Types; High, Medium, Low, and Matched
-
Flags
-
Dates & Times via a ‘picker’ and some presets
-
Created By
New table layout and functionality:
-
Introducing a Flags column
-
Column header searching and filtering
-
Column header date & time ‘picker’
-
Dockable Details pane, horizontal, vertical, or minimized
Flags
-
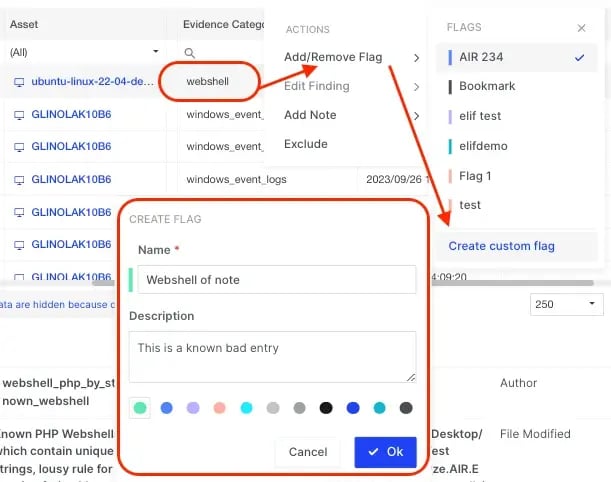
It is now possible to create custom flags by right-clicking on an evidence item, selecting ‘Add/Remove Flag’, and then creating a name, description, and color for your Flag:
-
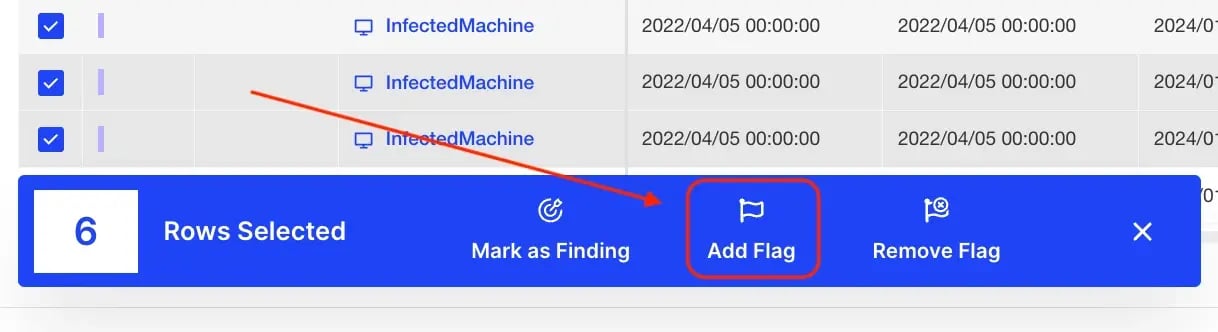
Select multiple items to perform Bulk Flagging operation:
-
Hovering over the flag in the table view will reveal:
-
The name of the flag
-
Who created the flag
-
The date & time it was created
-

-
Flags are saved at the Organization level in Libraries
-
Creating new flags or editing existing flags can be done here if the user has Case Management privileges.
-
The bookmark flag is a fixed/permanent flag.

User-generated Findings
-
AIR 4.13 has added user-generated Findings to complement AIR’s DRONE Findings
-
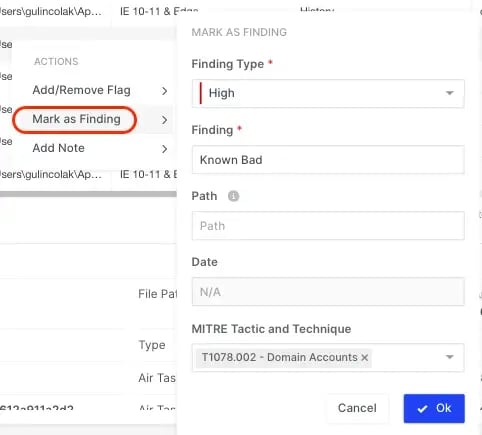
Right-clicking on an evidence item will allow users to allocate a Finding to the item
-
The user must select Finding Type and label the Finding
-
Users can also choose to detail the Path and attribute the Finding to a MITRE ATT&CK TTP
-
User-generated Findings are allowed only at the Case level.
-
Exclusions
-
It is now possible to select any evidence items from your Findings for exclusion.
-
Three options:
-
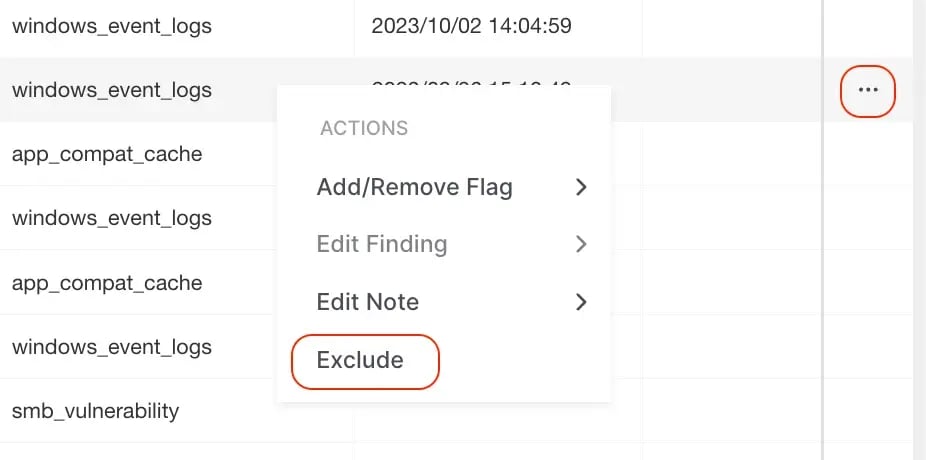
Right-click on a Finding and select ‘Exclude’
-
Select the ellipsis at the end of the row
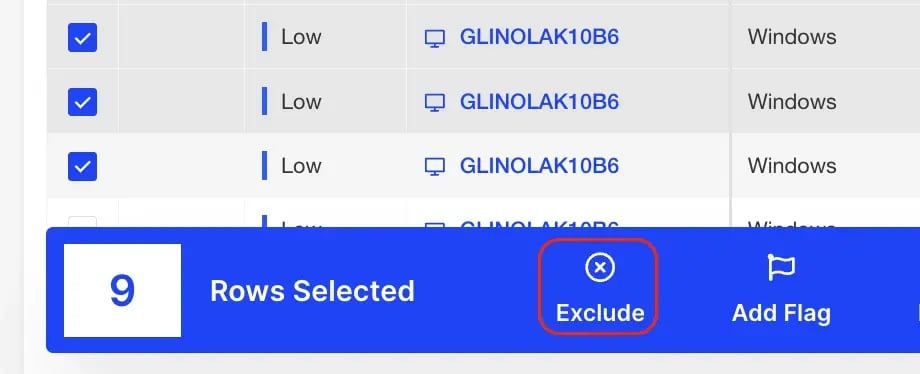
-
Bulk Actions will allow you to exclude more than one item at a time
-
-
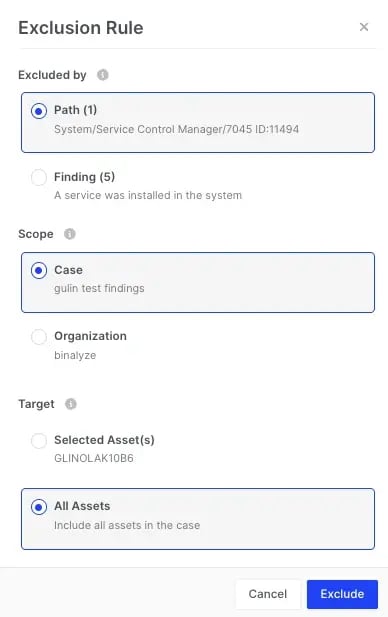
The Exclusion Rule allows you to exclude by:
-
Path or Finding
-
For the Case or whole Organization
-
For selected assets or all assets in the case
-
-
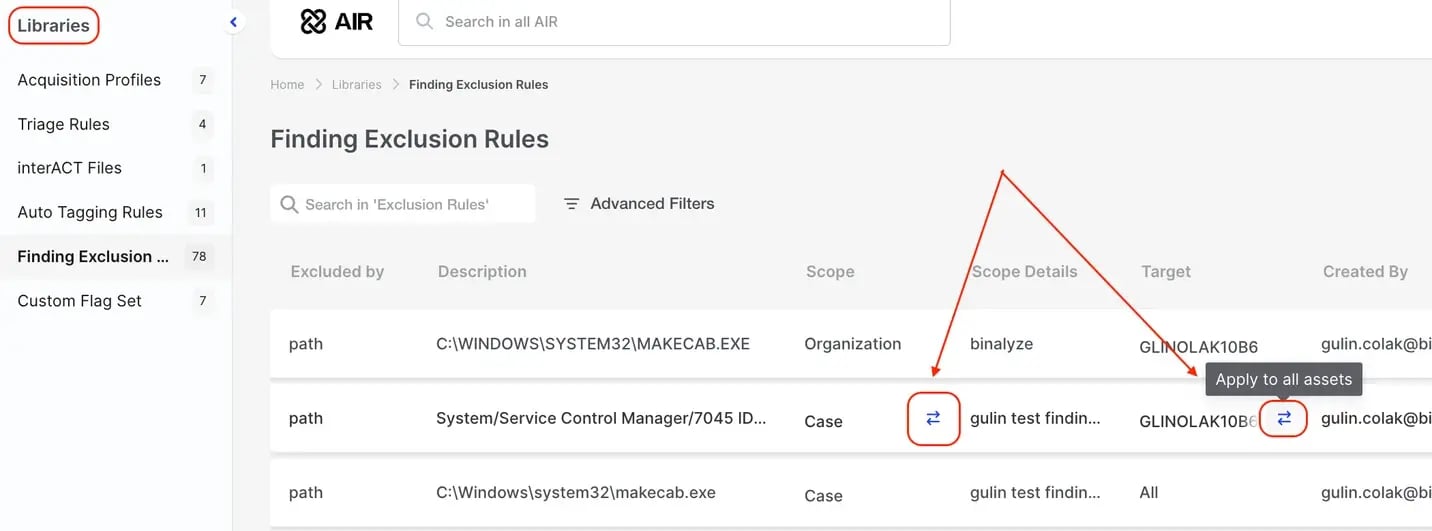
Exclusions are managed in the Organization Library where the Scope can be changed between Case or Organization.
-
The Target can be changed between one asset or all assets in the case - This is a one-way operation!
-
Deletion of the exclusion rule is only possible when the ‘Case Management’ privilege is granted
Notes
-
Notes can now be added to every evidence item - the item does not have to be bookmarked to have a note attached.
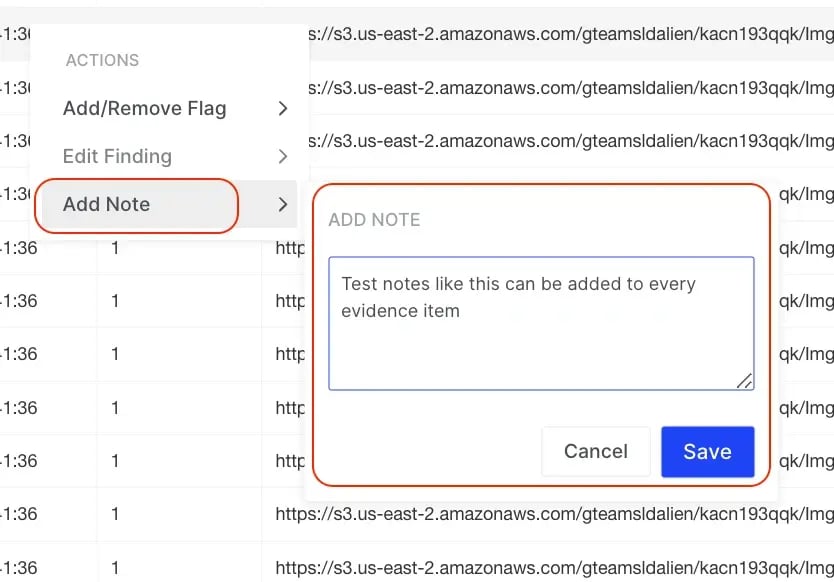
-
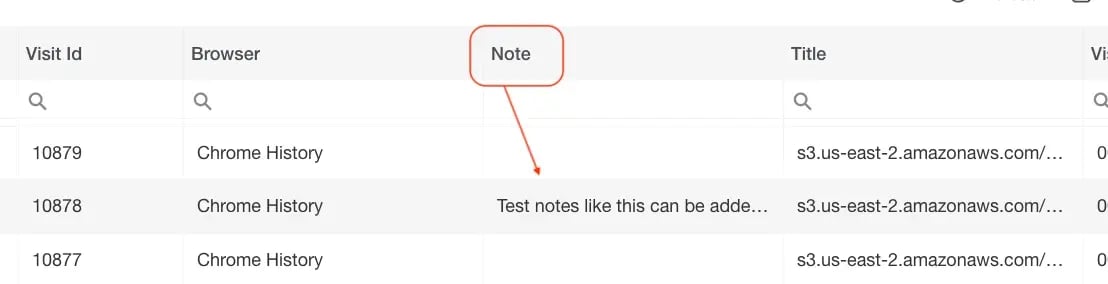
The new table view now has a Notes column for all items
-
Notes can be included in your reports
Improved Reports
-
The new flagging capability in the Investigation Hub improves reporting by enabling users to include specific Findings and further filter by individual Flags for a more targeted output:
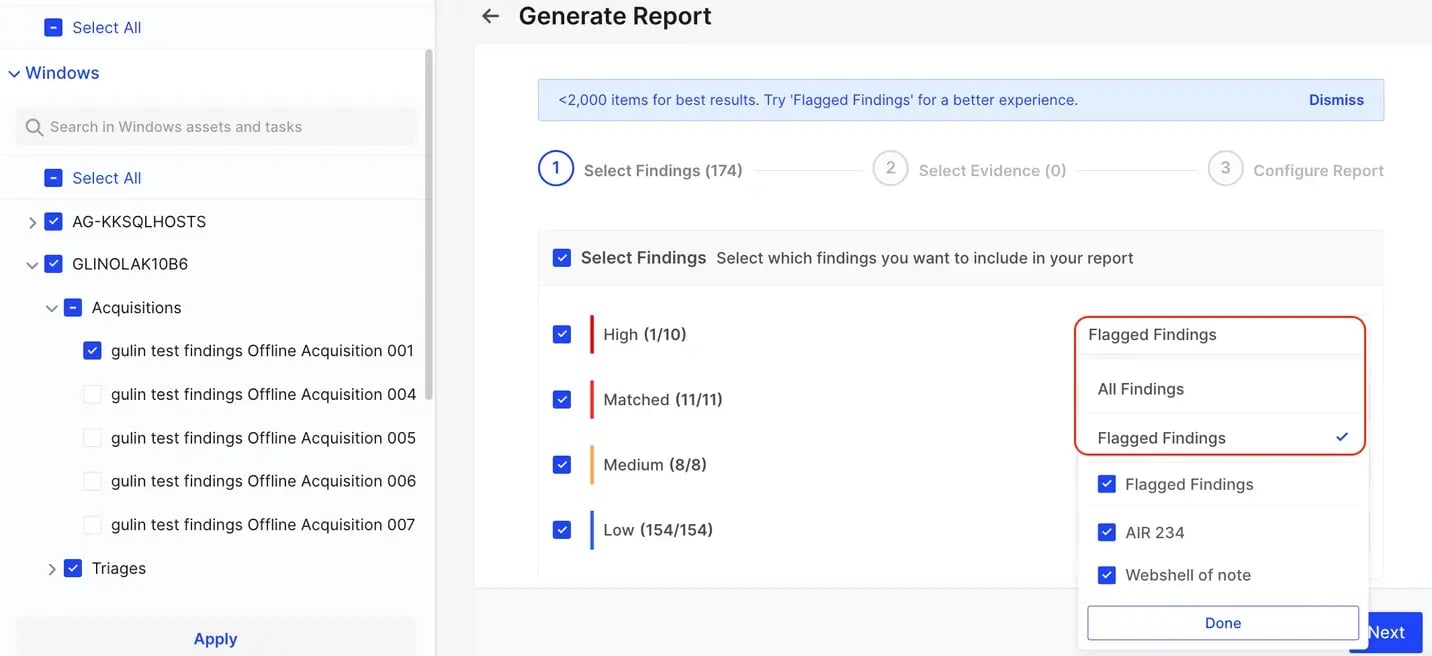
-
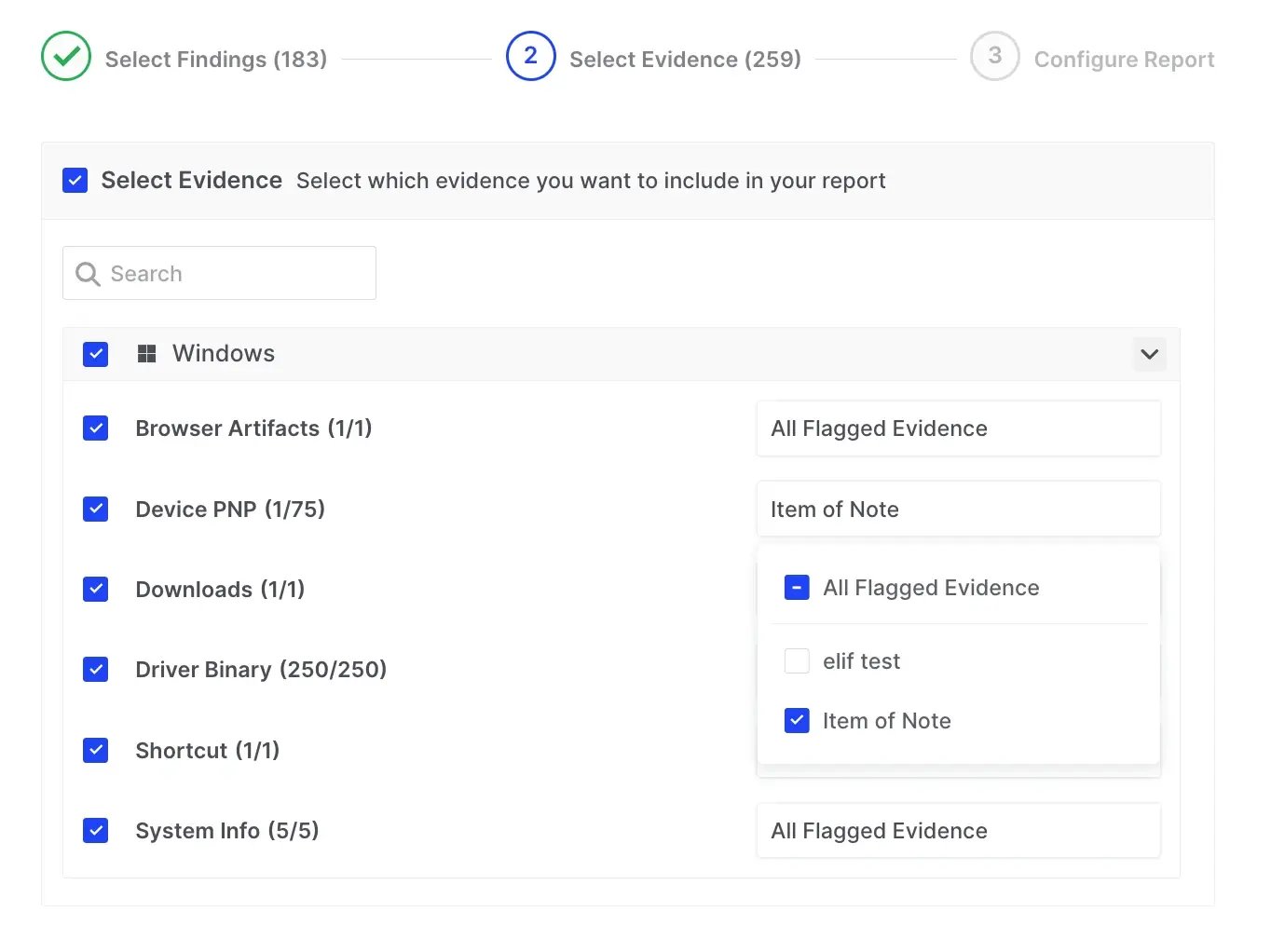
This enhanced granularity extends to the next step of report generation, where users can now add and filter non-finding evidence items by Flags for even more precise reporting:
For more information about the Investigation Hub please visit our Knowledge Base:
AIR Investigation Hub | Knowledge Base
-
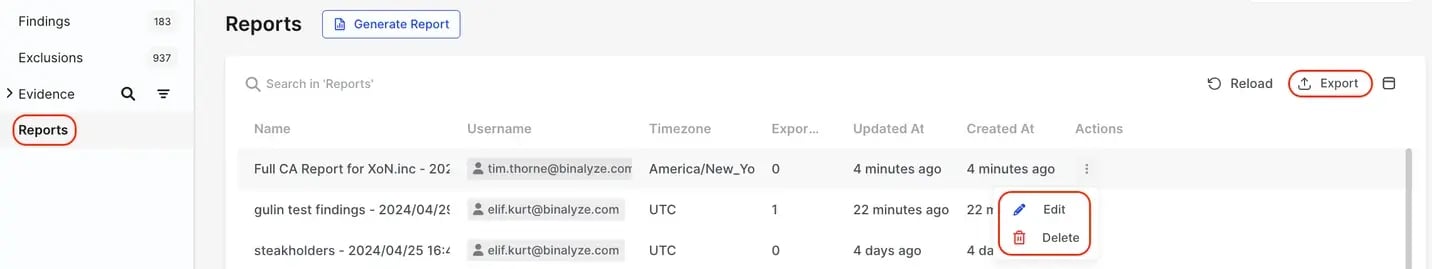
Reports can be managed, edited, generated, exported and deleted all from the Reports tab in the Secondary Menu:
Away from the Investigation Hub other new features include:
-
New Windows, macOS, and Linux evidence types:
|
Category |
Name |
Collection Type |
|
Browser |
Edge Sessions |
Parsed & presented in Investigation Hub |
|
Browser |
Opera Sessions |
Parsed & presented in Investigation Hub |
|
Browser |
Brave Sessions |
Parsed & presented in Investigation Hub |
|
Browser |
Vivaldi Sessions |
Parsed & presented in Investigation Hub |
-
New Windows evidence types:
|
Other Evidence |
Powershell ConsoleHost History |
AWAITS checking |
|
Browser |
QQ Sessions |
Parsed & presented in Investigation Hub |
-
New macOS evidence type:
|
Browser |
QQ Sessions |
Parsed & presented in Investigation Hub |
|
Browser |
Arc Sessions |
Parsed & presented in Investigation Hub |
-
New Linux evidence type:
|
Browser |
Chromium |
Parsed & presented in Investigation Hub |
-
osquery can be added to an Acquisition Profile
-
A new "osquery" tab has been added to the acquisition profiles for each supported OS, enabling users to enhance evidence collection by incorporating osquery capabilities into their evidential acquisitions.
-
Users have the option to "Validate Queries," which checks for and highlights any issues in a query before it is saved. Additionally, saving a query automatically triggers validation.
-
NB: This unique feature allows users to send data collected via osquery directly to a timeline, an option not available in previous osquery implementations for triage.
-

-
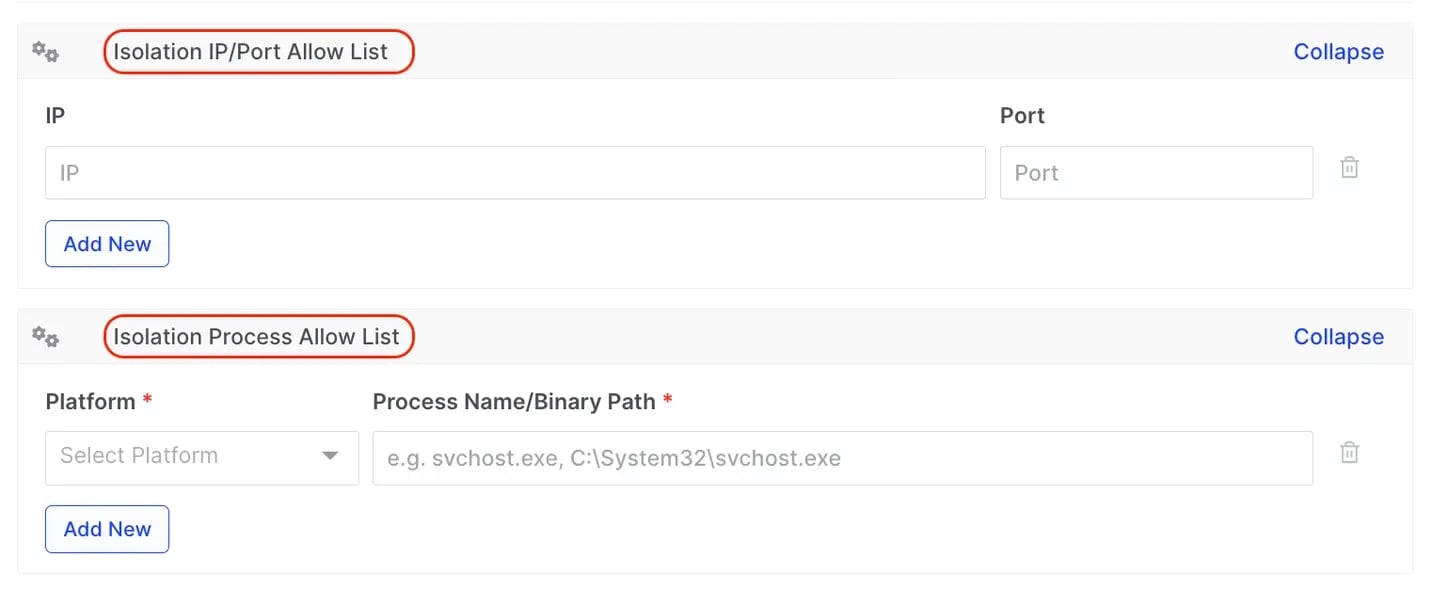
AIR Isolation ‘allow’ lists
-
Users can now specify a list of pre-approved processes, IP addresses, and ports that remain active on an isolated asset. This ensures that essential services and connections, such as EDR, continue uninterrupted, supporting ongoing SOC processes.
-
For IP and Port allowances, users can complete either one or both fields as needed and IP ranges are allowed.
-
For Process allowances, users must complete both the Platform and Process Name/Binary Path fields.
-
When specifying allowances, if a specific path is provided for the process, only that exact process will be permitted. If only the process name is listed, all instances of that process will be allowed.
-
NB: AIR policies do not aggregate; only the most recently applied policy takes effect.
-
Enhancements
-
Binalyze MITRE ATT&CK Analyzer has been updated to version 5.0.1
-
For details please see the changelog in the Binalyze KB.
-
-
User Privileges for Task Scheduling:
-
AIR administrators can now restrict users from scheduling tasks or editing existing ones:
-
Schedule Task: Enables users to "Schedule for later." Without this privilege, this option is disabled, and a tooltip explains the restriction.
-
Update Scheduled Task: Allows users to edit scheduled tasks. If this privilege is not granted, the "Edit" button is disabled with an explanatory tooltip.
-
-

-
Scheduling options for responder updates
-
New scheduling options for responder updates to streamline the process, ensuring that updates do not disrupt ongoing investigations.
-
Scheduled Manual Updates: Users can now schedule updates for a specific time for an individual asset or a group of assets. Setting a new update time for an asset will override any previously scheduled time for that asset.
-
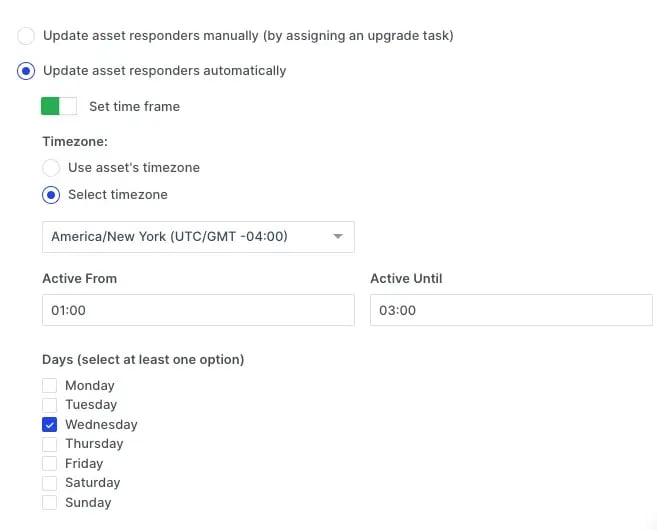
Scheduled Auto Updates: Users can establish a recurring schedule to automatically check for and apply updates within a designated timeframe.
-
The Assets > Settings page allows selection, timezone, times, and days of the week for the task to be executed.
-
-
-
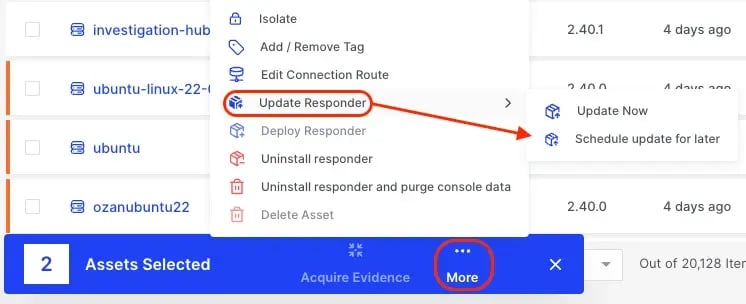
Alternatively, assets can be scheduled for responder updates either through the individual Asset action button or by using the bulk actions bar.
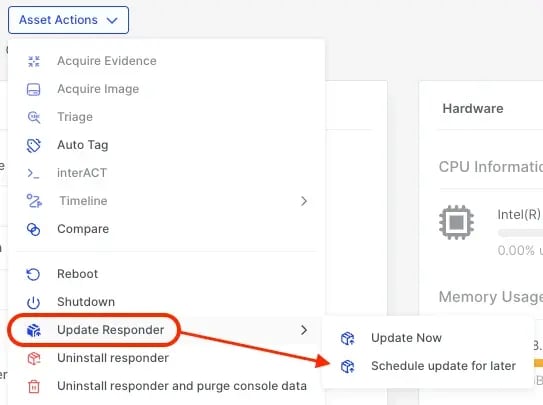
-
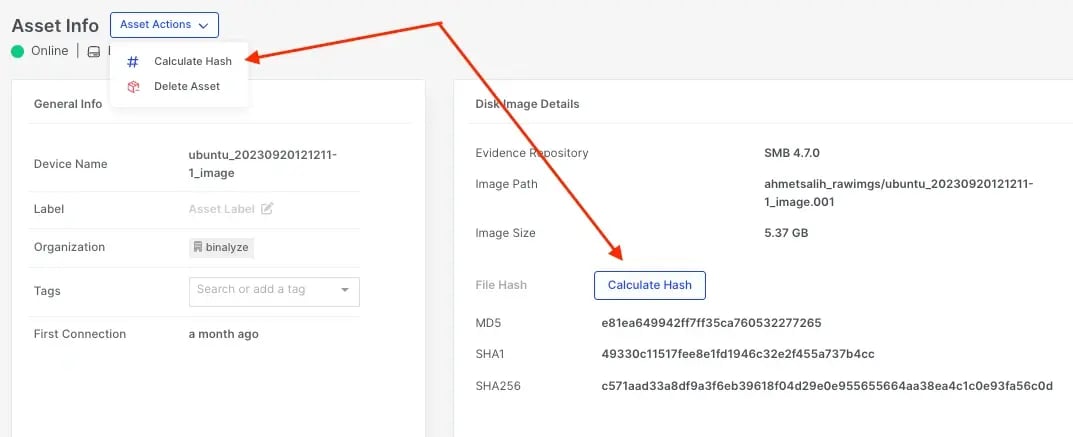
File Explorer - Calculate Hash for disk images
-
When a disk image is added as an asset to AIR, users can now calculate the hash value of that image file either through the Asset Actions button or from the Disk Image Details window.
-
MD5, SHA1 and SHA256 are all calculated simultaneously.
-
This hash function can be carried out at any time.
-
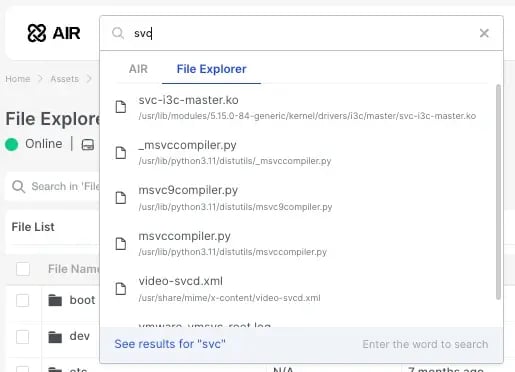
-
File Explorer - Recursive Search
-
Recursive searching is now possible in the AIR File Explorer via the Global Search box where the File Explorer tab will display any hits found in the File Explorer.
-
Fixes
-
Timeline date filtering issue has been fixed (Credit: Josh T)
-
Column widths changing automatically with no user interaction has been fixed. (Credit: Guo Y)
-
Off-line users Windows Registry data will now be parsed (Credit: Mark CD)










