
Covid-19 pandemic has become the most important topic in cyber security as in many other areas. The pandemic has affected people’s lives and caused significant changes in working procedures of organizations. Many organizations including public institutions activated remote working procedures hastily. In fact, the transition has emerged as an imperative to protect employees and to prevent the spread of the pandemic. So it is still unknown whether they are well prepared for the situation, even if they are practicing the work-from-home right now.
The image that has emerged so far do not give any idea of organizations’ preparation level, but it has clearly showed that there are many cyber attackers who try to exploit the situation caused by the pandemic. The increase in cyber incidents related to Zoom application (daily traffic to its download page increased 535 percent in the last month) which used by many organizations and work-from-home employees is one of the most obvious indicators. Another significant indicator is 32X increase in the number of successful daily phishing attacks. It is obvious that cyber criminals are adapting their techniques to new working environment.
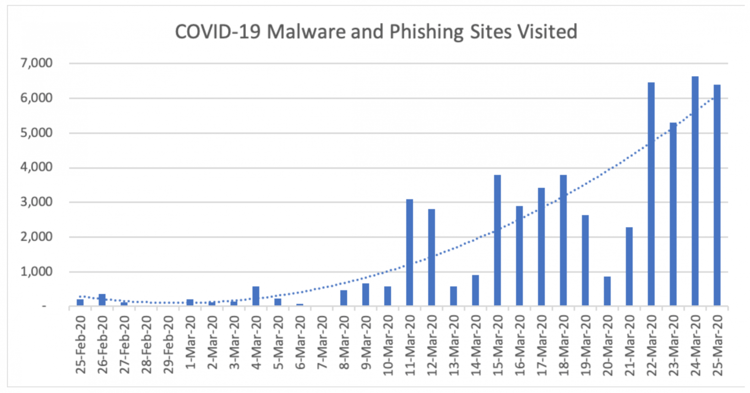
The organizations will face a serious examination because the increasing number of cyber incidents. The employees sitting in front the computer in the office before the pandemic had the capability to check the whole system physically in order to secure the network and the sensitive information of the organization are now at home and trying to do the same job. At this point, while it is now more difficult to supervise the employees working from home, on the other hand, more time may be needed to detect and respond to a possible cyber incident. Traditional methods, based on physical connection, used by the organizations can be insufficient to respond to incidents. So the organizations need a new perspective. Simple and fast applicable automated procedures and practices will make it easier to respond to incidents and minimize the damage by shortening the reaction time.
Covid-19 pandemic does not seem to end in the short term. So the increase in remote working related to the pandemic will not end soon as well. It is estimated that remote working emerged with the pandemic as a mandatory practice will increase 5-6 times in next two years. It will be better to be ready for this new working environment to be permanent after the pandemic.
Five measures to be taken:
-
Developing a new perspective: Developing a new perspective independent from traditional working pattern will be very helpful to solve the problems which are caused by remote working. When security and IT infrastructure of the organization is reviewed in terms of this perspective, it will be easier to find solutions to possible cyber incidents and determine necessary hardware, software and the need of qualified IT personnel.
-
Training of the employees: Most of the cyber incidents are based on users. Therefore training is of the employees will minimize the risk of a possible incident. Otherwise, even if all necessary measures are taken, the cyber incident is inevitable.
-
Preparing an Incident Response Plan: It vital to have a path to follow when a cyber incident occurs. Because in case of an incident knowing what to do step-by-step will help everyone (employees, IT personnel, experts, managers) and protect the organization from possible simple mistakes and waste of time. Developing an Incident Response Plan, will help organizations get out of the crisis where the time is so valuable and prepare them for future cyber threats.
-
Using VPN: Remote working (probably from a public network) inevitably will cause a need of remote access to organizations critical data. Creating an encrypted and secure tunnel to access the servers of the organization will reduce the risk of a cyber incident. You can make use of the VPN opportunities offered by operating systems as well as the commercial VPN providers.
-
Continuous IT Auditing: It is now more difficult to audit the computers and the network of organizations systematically and to keep the system under control with hasty transition to remote working. This process made the organizations more vulnerable to cyber-attacks. Creating an auditing system for the employees away from IT personnel of the organizations, without a secure internet connection, connecting organizations’ servers from various locations is a mandatory issue to prevent cyber incidents and minimize the response time.










